
Discover SecurityVulnerabilities
Find exposed credentials, configuration files, and database backups before attackers do. Use powerful regex patterns with transparent, pay-per-search pricing.
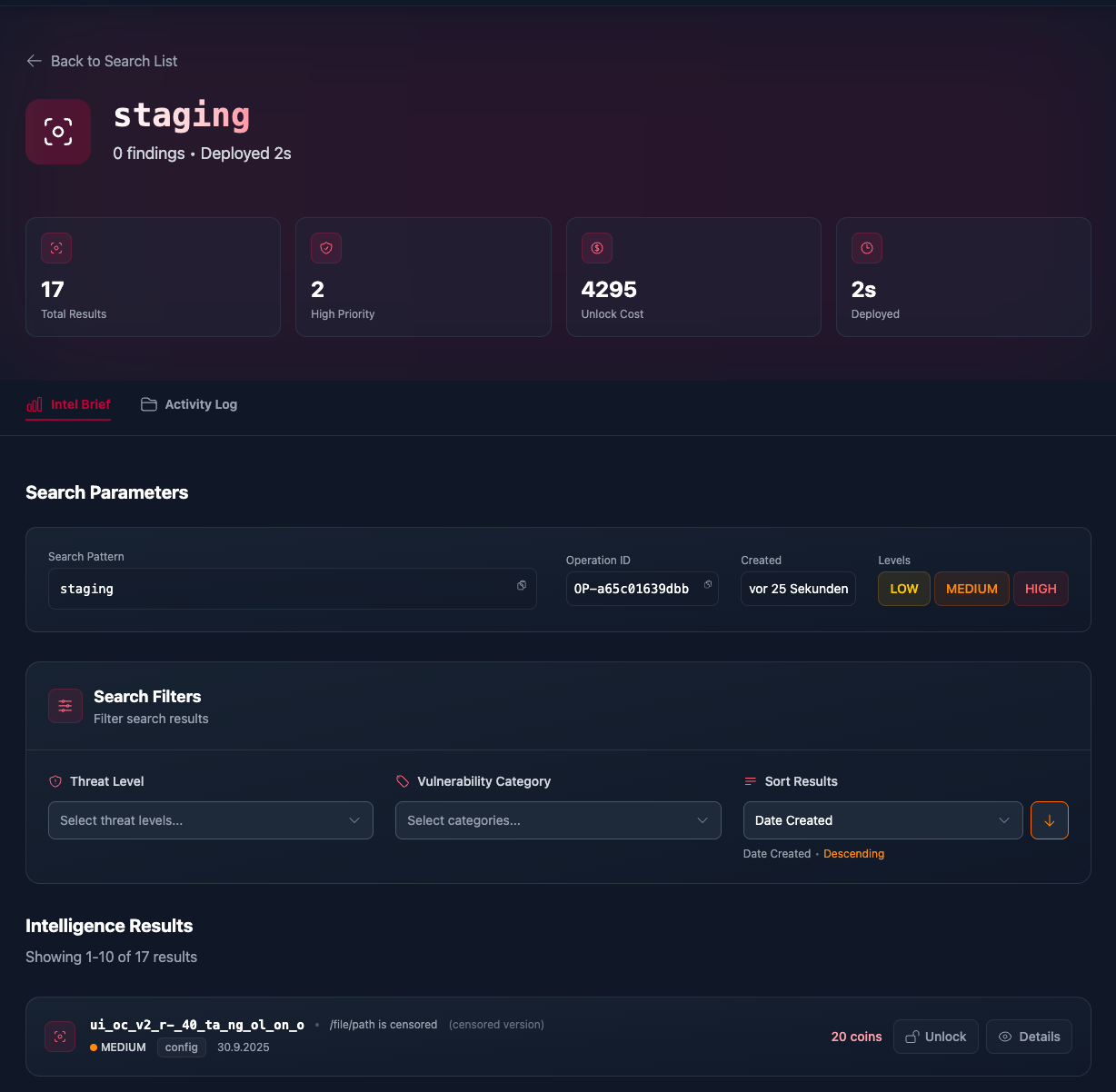
Discover Critical Security Exposures
Search across multiple vulnerability categories to find exposed data before it becomes a breach
Configuration Files
Find exposed config files and settings that may contain sensitive information
Source Code
Search for leaked source code that may expose business logic or secrets
WordPress Issues
Misconfigured WordPress installations with potential vulnerabilities
Outdated Software
Identify vulnerable software versions that need updating
Credentials
Find exposed passwords, API keys, and authentication data
Database Backups
Locate exposed database files and backups
Exposed Files
General file exposure vulnerabilities
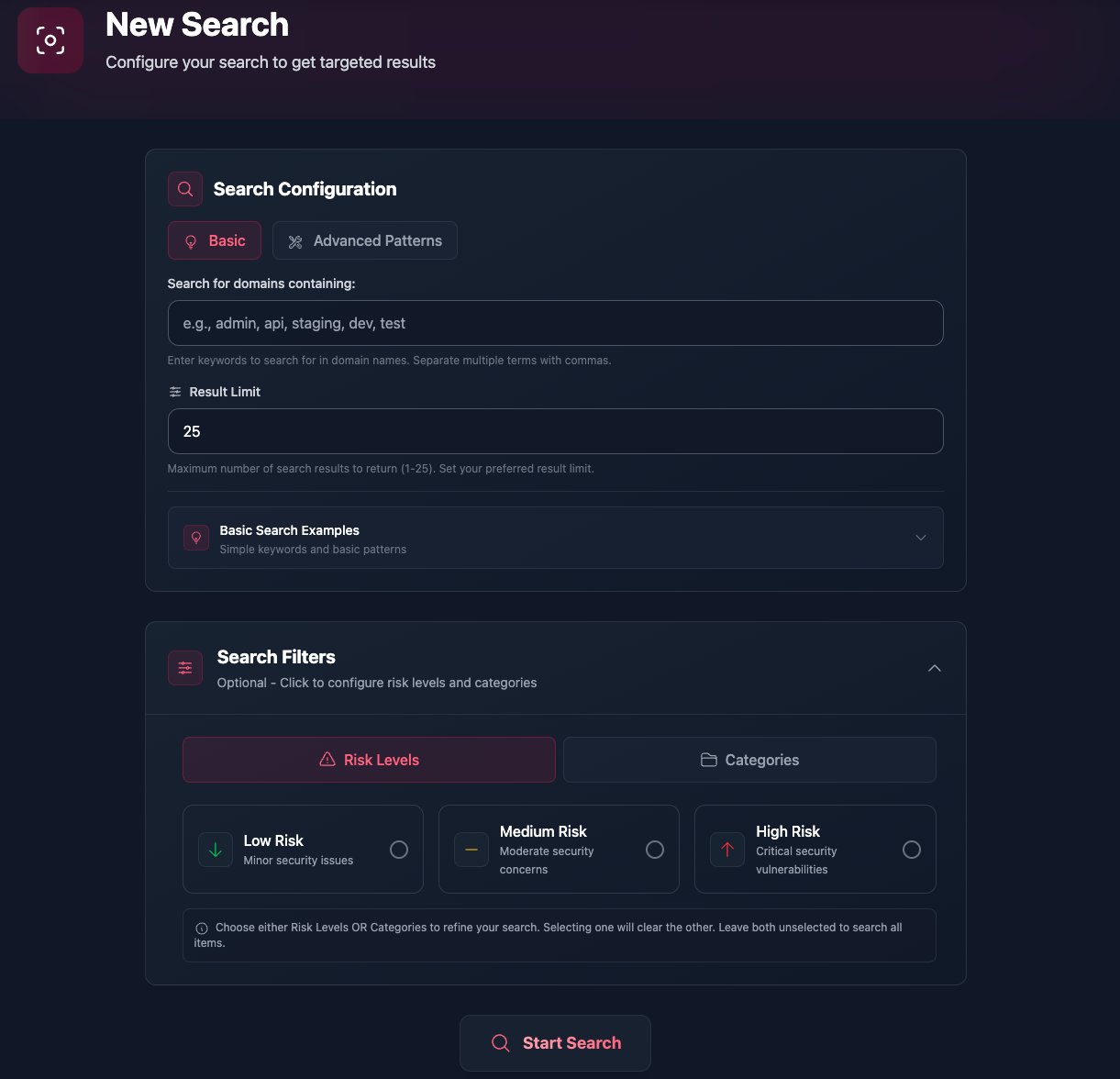
Powerful Regex Search
Use advanced regular expression patterns to find exactly what you're looking for. Choose between basic mode for simple searches or advanced patterns for complex queries.
Pattern Matching
Advanced regex support for precise vulnerability discovery
Filter & Sort
Organize results by criticality, category, and date
Search History
Track all your searches and access results anytime

Categorized Results
Every finding is categorized and rated by criticality level. Filter results, report false positives, and maintain organized security intelligence.
Criticality Ratings
Risk levels help prioritize your security response
Detailed Information
Domain, path, category, and discovery details for each finding
False Positive Reports
Improve accuracy by reporting incorrect findings
Why Choose Cerast Intelligence
Security intelligence designed for efficiency and transparency
Regex-Powered Search
Use advanced regular expressions to find exactly what you're looking for across domains and exposed data.
Instant Results
Get fast search results with categorized findings and criticality ratings to prioritize your response.
Multiple Categories
Search across credentials, configs, databases, source code, and other vulnerability categories.
Transparent Pricing
Pay only for what you use with our coin-based system. No monthly fees or hidden charges.
Search History
Track all your searches and access results anytime. Your findings never expire.
Referral Program
Earn credits by referring others. Share your code and both you and your referrals get bonus coins.
Simple, Transparent Pricing
No monthly subscriptions. Pay only for the searches you need with our coin-based system.
How It Works
Pay per search, no commitments
Purchase Coins
Buy coin packages via secure Stripe payment
Run Searches
Each search costs coins based on scope
Get Results
Access your findings anytime, no expiration
No Subscriptions
Pay only when you search. No recurring charges or commitments.
Secure Payments
All transactions protected by Stripe's industry-leading security.
Referral Rewards
Earn credits by referring others. Share your code and both benefit.
Start Finding Vulnerabilities Today
Join security professionals using Cerast Intelligence to discover exposed data and protect their infrastructure. Get instant access with no commitments.